In March 2025, we conducted another phishing test to evaluate our organization’s resilience against phishing attacks. This test was particularly challenging, yet it provided valuable insights into our cybersecurity awareness. Out of 507 recipients, 64 failures occurred from the phishing test.
We are incredibly thankful to the 165 individuals who reported the phishing email. The first report came in just one minute after the campaign was launched! Reporting phishing emails, even if you fail the test, is crucial for our institution’s cybersecurity. It allows us to quickly identify and mitigate potential threats, protecting our organization and its members from harm.
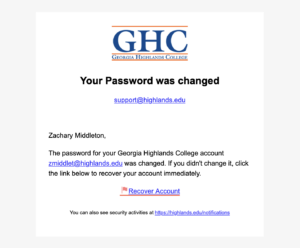
Below, we outline the key indicators from our test that everyone should be aware of:
Ambiguous Salutations: Be cautious of generic greetings like “Hello” or “Dear user.” Legitimate emails from our organization will usually address you by name (not in this particular case, but please be aware of this common indicator).
Sense of Urgency: Phishing emails often create a sense of urgency to prompt immediate action. In our test, the email urged recipients to recover their account immediately if they didn’t change their password.
Hover Over Links: Always hover over links to check if the URL matches the site it claims to be. In our test, the link provided did not lead to the official site.
Spelling/Grammar Errors: Watch out for spelling and grammatical mistakes. Although not shown in our test email, errors like these are common in phishing attempts.
Suspicious Sender Address: Even if the sender’s address appears to be from our organization, it could be spoofed. Always verify the sender’s email address carefully.
By staying alert and recognizing these red flags, we can better protect ourselves and our organization from phishing attacks. Remember, if something feels off, it’s always better to double-check before taking any action and please utilize the “Phish Alert Button”.