Test Inspiration:
In early 2023, Cloudflare detected and blocked a phishing campaign leveraging the Microsoft brand in an attempt to harvest credentials through a legitimate — but compromised — site.
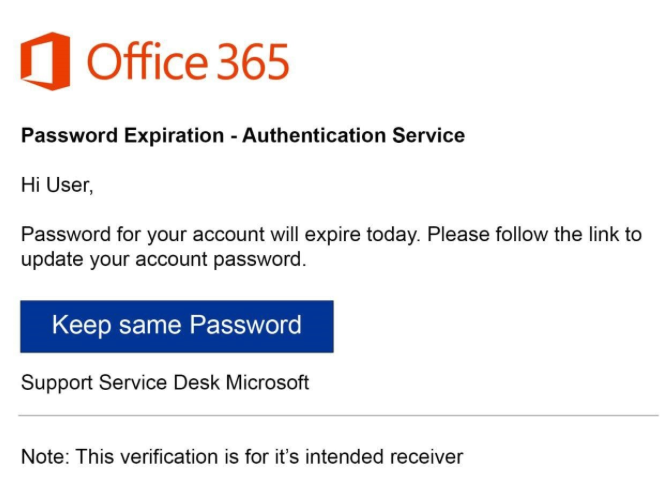
Phishing Email Context: The phishing email designed for this test mimicked an official Microsoft password expiration notification. It used a personalization messaging such as the Office 365 logo and posing as “Support Service Desk Microsoft”. If you hovered over the Link, you would see that it would direct you to the malicious domain “confirmed.successful[.]org“. The design and content were tailored to look authentic, making it challenging for users to distinguish it from a legitimate Microsoft password expiration message.
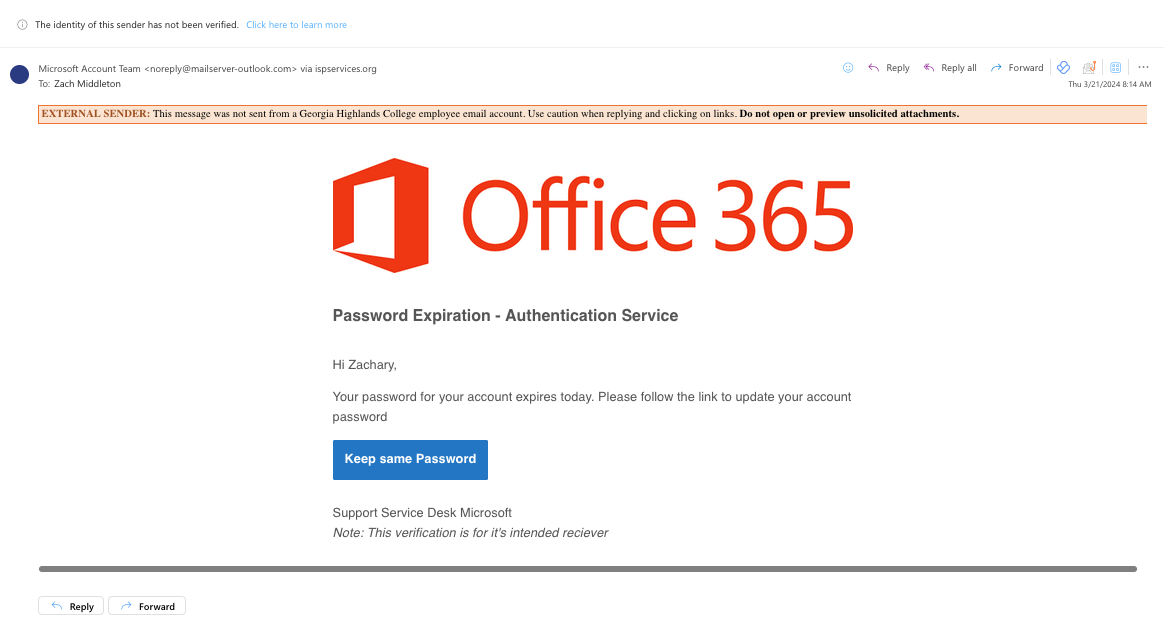
![]()
Key Findings & Recommendations:
- Email Address Discrepancies: Be cautious with emails that appear genuine but have slightly altered addresses. Cybercriminals often use domains that resemble the authentic one with minor changes.
- Suspicious Links & Attachments: Always approach links or attachments in unsolicited or unexpected emails with suspicion. They are common phishing tactics.
- Verify Links: Before engaging with any link, hover over it to inspect the actual URL. Ensure it directs to a legitimate site and be alert for any anomalies like misspellings or odd domain extensions.
- Check for Personalization: Authentic communications, especially from platforms like Microsoft Teams, will often be personalized. Beware of generic greetings.
- Stay Updated: With cybercriminals constantly refining their methods, it’s crucial to stay updated on the latest phishing strategies and partake in regular awareness training.
- Report Suspicious Emails: If you encounter a dubious email, refrain from interacting and promptly report via the Phish Alert button.
Conclusion: The landscape of phishing is continuously changing. By staying informed about cybercriminals’ tactics and maintaining a vigilant approach, we can substantially mitigate the risk of succumbing to these threats.
References: https://blog.cloudflare.com/2023-phishing-report/